Brian Vermeer
Java Champions & Developer Advocate and Software Engineer for Snyk.
Passionate about Java, (Pure) Functional Programming, and Cybersecurity. Co-leading the Virtual JUG, NLJUG and DevSecCon community.
Brian is also an Oracle Groundbreaker Ambassador and regular international speaker on mostly Java-related conferences.
Step up your coding with the Continuous Feedback Udemy Course: Additional coupons are available
What do you know about the code changes that were just introduced into the codebase? When will you notice if something goes wrong?
Stable, Secure, and Affordable Java
Azul Platform Core is the #1 Oracle Java alternative, offering OpenJDK support for more versions (including Java 6 & 7) and more configurations for the greatest business value and lowest TCO.
Jakarta EE 11: Beyond the Era of Java EE
This user guide provides a brief history of Java EE/Jakarta EE and a detailed overview of some of the specifications that will be updated in Jakarta EE 11.
Do you want your ad here?
Contact us to get your ad seen by thousands of users every day!
[email protected]How Chat Memory Manipulation Can Ruin Your AI System
Table of Contents Do LLMs have any conversational memory?Implementing chat memory in your AI appChat messages with Java’s Langchain4JLLM chat memory injectionChat memory injection: Proof of conceptPreventing chat memory manipulation is key Do LLMs have any conversational memory? With the ...
Table of Contents Understanding LLM guardrailsHow guardrails workEasily implementing guardrails with QuarkusInput guardrailsOutput guardrailsSanitizing LLM input and output Integrating Large Language Models (LLMs) into our applications is becoming increasingly popular. These models are extremely useful for creating content, searching documentation, …
Table of Contents VideoPodcast AppsContent On May 13th and 14th, Foojay attended the JCON conference in Köln, Germany, where we did over 30 live-stream interviews. In this episode, we present to you the first set of these interviews, in which …
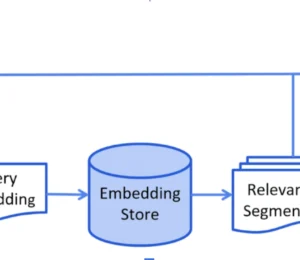
Table of Contents Why use RAGHow RAG Works1. Retrieval2. GenerationSecurity implications of using RAGPrompt injection through retrieved contentData poisoningAccess control gaps in retrievalLeaking PII to third-party modelsCaching risks and session bleedContradictory or low-quality informationProactive and remediation strategies for securing RAGSanitize …
Table of Contents CVE-2025-0851 explainedAbsolute Path TraversalRemediation Deep Java Library (DJL) is an open source deep learning framework that brings AI capabilities to Java developers without requiring a shift to Python. It provides an intuitive, high-level API for building, training, …
Table of Contents What are SBOMs?Why do we need SBOMs?Creating SBOMs with the Snyk CLIInstalling the Snyk CLIGenerate SBOMs using the Snyk CLIMultiple projectsAutomating SBOM generation with the Snyk CLIAnalyzing SBOMsSnyk CLI SBOM TestSupplying up-to-date SBOMs with Snyk The software …
Table of Contents VideoPodcast AppsGuestsJonathan VilaBrian VermeerErik CostlowContent Three years after Log4Shell caused a significant security issue, we still struggle with insecure dependencies and injection problems. In this podcast, we’ll discuss how developers can secure their code. I talked with …
Table of Contents The developer’s dilemmaThe current state of Log4shellMore than 20% of companies are still vulnerable to Log4shell.Spring4Shell in the wildWakeup call to all who maintain applications This article was originally published at Snyk.io As developers, we’re constantly juggling …
Nowadays, the security of your applications is just as important as the functionality they provide.
Encryption is converting readable data or plaintext into unreadable data or ciphertext, ensuring that even if encrypted data is intercepted, it remains inaccessible to unauthorized individuals.
Keeping your dependencies in check is crucial to ensure that your Spring Boot projects run smoothly and remain resilient in the face of ever-evolving threats.
So happy to see @OpenJDK uses #SonarCloud to guarantee High #CodeQuality for @java #Java25 @SonarSource
https://bugs.openjdk.org/browse/JDK-8357798
The hottest #Java unconference in the world is coming back 27-31 July 2026 (starting evening of 26th). Deep discussions about Java and life. We are making some seats available using a lottery system. Draw will be on Friday the 20th Feb. Sign up here: https://www.jcrete.org/lottery
Confession: I usually lose the Flow switching between Quality Gates and Code 📉😅
But I connected @claudeai + #SonarQube via #MCP
Verify & Fix vulnerabilities without touching the mouse.
Zero context switching. Pure flow. 🚀
https://foojay.io/today/claude-code-sonarqube-mcp/
#Java #AI @foojayio