Getting Started with Snyk for Secure Java Development
- July 29, 2021
- 5276 Unique Views
- 4 min read
If you’re a Java developer who wants to develop your applications more securely, you’ve come to the right place. Snyk can help you with that mission.
This article will explain how to begin with Snyk for secure Java development so you can be more secure from the get-go.
If you’re new to Snyk, it’s important to know that we offer a variety of developer-focused products and tools. Some of these tools, like our CLI and some IDE integration, support multiple products. However, we can distinguish four different products within Snyk:
- Snyk Open Source – Securing your open source dependencies
- Snyk Container – Securing your container images
- Snyk Infrastructure as Code (Snyk Iac) – Securing your infrastructure as code
- Snyk Code – Securing your custom code. In this post, we’ll focus only on Java.
To get started with these tools, you’ll need to sign up for a free Snyk account. For solo developers, our Free plan is usually more than enough for your needs, so keep your credit card in your wallet.
After you have signed up, there are multiple ways to engage with Snyk for Java. I will explain this tool by tool below.
Snyk CLI
The Snyk CLI is the most accessible tool to start with Snyk for Java. You can install it in multiple ways using npm or brew, for instance:
npm install -g snykThis tool is great for your local machine and can also be a super useful tool for your CI pipeline. The first thing you need to do is authenticate the snyk CLI by either setting your API token as an environment variable (recommended for CI systems) or calling snyk auth.
Testing your Java project for security issues in your open source dependencies is as easy as calling snyk test for the root of your project. Depending on the build system you use for Java, make sure that either Maven or Gradle are installed and available. The Snyk CLI uses your package manager and pom.xml or build.gradle to get the entire dependency tree. Please ensure that your project is built using Maven or Gradle before calling a snyk test to prevent unexpected results.
When your project contains multiple manifest files, like multiple pom files. Use the --all-projects flag to scan all your projects. This also works if you have for instance, a Gradle Java project combined with a JavaScript frontend using npm. Lastly, use the --help flag to find specific settings for either Maven or Gradle.
Check out the CLI cheat sheet for more tips and tricks on the Snyk CLI. You can use the same CLI to scan your containers for security issues and your infrastructure as code (IaC). In addition, we will soon be releasing Snyk Code for the CLI, which helps to prevent security vulnerabilities in your custom Java code.
Connecting your Java project’s Git repository
Next, you can connect your Git repository. If you connect your Java repository, for example Github, Snyk automatically searches for your Maven or Gradle manifest file and scans your dependencies. By default, this action will be repeated daily, and you will get notified whenever a new security vulnerability or a new fix is found in your repository.
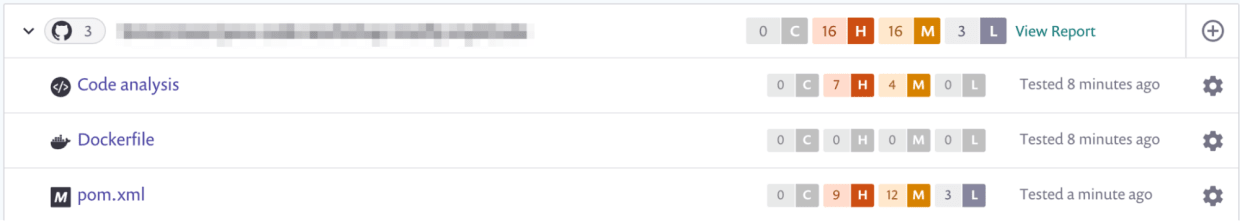
The example below shows a pom file from a demo project that contains known security vulnerabilities. Every time Snyk finds a new issue, it will be visible in your dashboard, explaining the vulnerability and possible remediation advice.
In addition, the get integration can also scan Dockerfiles and perform Snyk Code analyses. If you want more information about the Snyk Code analyses for Java applications with the Snyk Git integration, check out this Solving Java security issues in my Spring MVC application blog post.
Maven and Gradle plugins
Some people prefer to automate their security testing during their builds. Naturally, you can do this inside a CI pipeline. However, it might make more sense to do this in your build tool. If you use either Maven or Gradle, this is the point where your dependencies get pulled in, and where the artifact is created. Why not automate security scanning in the same way as we do with unit testing? Snyk provides both a Maven and Gradle plugin. The only thing you need is an API key that you can get from your free account.
Now you either call a snyk test from both Maven and Gradle manually or connect to a specific task when building your application. Check out the dedicated articles on the Maven plugin and the Gradle plugin for Snyk.
- Snyk Maven plugin: Integrated security vulnerability scanning for developers
- Gradle dependencies: scanning with new Snyk Gradle plugin
Snyk Java IDE plugins
Some developers are more comfortable doing everything from their IDE. To some extent, the IDE nowadays is like a swiss army knife with a tremendous amount of options and extensibility. Some developers practically live in their IDE.
Recently, in the JVM Ecosystem report 2021 we found out that IntelliJ IDEA, Eclipse, and VS Code are the top three IDEs for Java development. For all three of these, Snyk has IDE plugins available.
Check out the following articles for more information on the specific plugins.
- How to fix Java security issues while coding in IntelliJ IDEA
- Fix open source vulnerabilities directly from your Eclipse IDE
- Visual Studio Code extension for Snyk Code
It is easy to start with Snyk
As you can see, starting with Snyk and creating secure Java applications doesn’t have to be hard.
Pick and choose the options that fit your way of working so that you can develop fast and stay secure.
Also know that we have a ton of integrations for different CI/CD pipelines if that suits you better.
In any case, Snyk offers everything a Java developer needs to build securely from the start!
Don’t Forget to Share This Post!





Comments (0)
No comments yet. Be the first.